Valid Tips For 100% Pass Exam 70-680: PassLeader now is providing the best 580q 70-680 VCE dumps and PDF dumps for your 70-680 certification exam. We offer the latest 580q 70-680 exam questions to ensure that you can 100 percent pass 70-680 exam, and what’s more, we will offer you the new updated 70-680 exam dumps for one year free and free new version VCE Player. Welcome to visit our site — passleader.com and get the valid 580q 70-680 braindumps to pass exam as soon as possible.
keywords: 70-680 exam,580q 70-680 exam dumps,580q 70-680 exam questions,70-680 pdf dumps,70-680 vce dumps,70-680 practice test,70-680 study guide,TS: Windows 7, Configuring Exam
QUESTION 31
You have a computer named Computer1 that runs Windows 7. Computer1 is a member of an Active Directory domain. Remote Desktop is enabled on the computer. You share a folder on Computer1. You need to configure Computer1 to meet the following requirements:
– Allow computers in the local subnet to access the shared folder.
– Prevent computers in remote subnets from accessing the shared folder.
– Allow all computers to connect to Computer1 by using Remote Desktop.
What should you do?
A. Modify the subnet mask.
B. Modify the Public folder sharing settings.
C. Disable network discovery on all computers located in remote subnets.
D. Modify the properties of the File and Printer Sharing firewall exceptions.
Explanation:
Network ProfilesNetwork profiles are important because you can use them to apply different collections of firewall rules based on which network profile is active. A significant difference between Windows Vista and Windows 7 is that in Windows 7, profiles apply on a per-network interface basis. This means that if you have one network adapter connected to the Internet and another connected to your office LAN, different sets of rules apply for each connection. The firewall in Windows Vista chooses the most restrictive network profile when a computer has connections to different network types and applies the most restrictive set of rules to all interfaces.Allowing Programs Through Windows FirewallWindows Firewall allows you to configure exceptions based on programs. This differs from Windows Vista where Windows Firewall would allow you to configure exceptions based on port address. You can still create rules based on port address; you just have to do it using WFAS, covered later in this lesson. You can also allow specific Windows 7 features, such as Windows Virtual PC, through Windows Firewall. Feature rules become available when you enable the feature using the Programs And Features item in Control Panel. To add a rule for a feature or program, click Allow A Program Or Feature Through Windows Firewall item in the Windows Firewall section of Control Panel. The figure shows a list of currently installed features and any programs for which rules have been created as well as the profiles for which rules concerning those programs and features are enabled.
File and Printer Sharing
This feature is used for sharing local files and printers with other users on the network. (Uses NetBIOS, LLMNR, SMB and RPC)
QUESTION 32
You have a computer that runs Windows 7. You attempt to add files to %programfiles%\app1 and receive a prompt to elevate your privileges. You need to ensure that you can add files to %programfiles%\app1 without receiving a prompt for elevated privileges. The solution must prevent harmful applications from making unwanted changes to the system. What should you do?
A. Enable the built-in administrator account.
B. Modify the User Account Control (UAC) settings.
C. Add your user account to the local Power Users group.
D. Modify the permissions of the %programfiles%\app1 folder.
Answer: D
Explanation:
In order to secure a computer and its resources, you must consider the rights that users will have. You can secure a computer or multiple computers by granting users or groups specific user rights. You can help secure an object, such as a file or folder, by assigning permissions to allow users or groups to perform specific actions on that object.
QUESTION 33
You have a computer that runs Windows 7. You configure the computer to automatically install all updates. You need to verify whether a specific update is installed. What should you do?
A. In event viewer, examine the application log.
B. In windows update, examine the update history.
C. At the command prompt, run Wusa.exe and specify the /kb parameter.
D. At the command prompt, run Verifier.exe and specify the /query parameter.
Answer: B
QUESTION 34
You have a computer that runs Windows 7. You need to identify which hardware is required to create a system repair disc. What hardware should you identify?
A. CD/DVD burner
B. Floppy disk
C. Tape drive
D. USB disk
Answer: A
QUESTION 35
You have a computer that runs Windows 7. You manually create a system restore point. You need to restore a copy of a file stored on a drive C from two days ago. You must act with minimum administrative effort. What should you do?
A. From recovery, select System Restore.
B. From Backup and restore, select Restore my files.
C. From the command prompt, run Wbadmin get items.
D. From the properties of the file, select Previous Versions.
Answer: D
QUESTION 36
You have a computer that runs Windows Vista. The computer has one partition and 1 GB of RAM. You need to upgrade the computer to Windows 7. What should you do?
A. Add 1 GB of RAM.
B. Create a second partition.
C. Disable User Account Control (UAC).
D. Install Windows Vista Service pack 2 (SP2).
Answer: D
Explanation:
You should keep the following in mind prior to and during the upgrade from Windows Vista to Windows 7:
– Perform a full backup of the computer running Windows Vista prior to performing the installation.
– That way, if things go wrong, you can do a full restore back to Windows Vista.
You must ensure that Windows Vista has Service Pack 1 or later installed before you can upgrade it to Windows 7.
– Ensure that you have the Windows 7 product key prior to the upgrade.
– You cannot upgrade between processor architectures. An x86 version of Windows Vista cannot be upgraded to an x64 version of Windows 7, and vice versa.
– You can upgrade only to an equivalent or higher edition of Windows 7.
– You can upgrade Windows Vista Home Premium to Windows 7 Home Premium, Professional, Enterprise, or Ultimate, but not to Windows 7 Starter. Windows 7 Professional is equivalent to Windows Vista Business.
– Ensure that there is at least 10 GB of free disk space on the Windows Vista volume prior to attempting the upgrade.Requirements:Windows 7 Home Premium, Professional, Ultimate, and Enterprise editions have the following minimum hardware requirements:
– 1 GHz 32-bit (x86) or 64-bit (x64) processor
– 1 GB of system memory- A 40-GB hard disk drive (traditional or SSD) with at least 15 GB of available space
– A graphics adapter that supports DirectX 9 graphics, has a Windows Display Driver Model (WDDM) driver, Pixel Shader 2.0 hardware, and 32 bits per pixel and a minimum of 128 MB graphics memory
QUESTION 37
You have a computer that runs Windows 7. The computer is configured as shown in the following table:
You plan to install a new application that requires 40 GB of space. The application will be installed to C:\app1. You need to provide 40 GB of free space for the application. What should you do?
A. Create a shortcut.
B. Create hard link.
C. Create a mount point.
D. Change the quota settings.
Answer: C
Explanation:
Assign a mount point folder path to a driveYou can use Disk Management to assign a mount-point folder path (rather than a drive letter) to the drive. Mount-point folder paths are available only on empty folders on basic or dynamic NTFS volumes.Volume Mount PointsVolume mount points are new system objects in the internal namespace of Windows 2000 that represent storage volumes in a persistent, robust manner. This feature allows multiple disk volumes to be linked into a single tree, similar to the way Dfs links remote network shares. You can have many disk volumes linked together, with only a single drive letter pointing to the root volume. The combination of an NTFS junction and a Windows 2000 volume mount point can be used to graft multiple volumes into the namespace of a host NTFS volume. Windows 2000 offers this new mounting feature as an alternative to drive letters so system administrators can transcend the 26-drive letter limit that exists in Windows NT. Volume mount points are robust against system changes that occur when devices are added or removed from a computer. Important-icon Important A volume is a self-contained unit of storage administered by a file system. The file system that administers the storage in a volume defines a namespace for the volume. A volume mount point is a directory name in an NTFS file system that denotes the root of an arbitrary volume. A volume mount point can be placed in any empty directory of the namespace of the containing NTFS volume. Because volumes can be denoted by arbitrary directory names, they are not required to have a traditional drive letter. Placing a volume mount point on an NTFS directory causes the storage subsystem to resolve the directory to a specified local volume. This “mounting” is done transparently and does not require a drive letter to represent the volume. A Windows 2000 mount point always resolves to the root directory of the desired volume. Volume mount points require that the version of NTFS included with Windows 2000 be used because they are based on NTFS reparse points.
QUESTION 38
You have a computer that runs Windows 7. You log on to the computer by using a user account that is a member of Administrator Group. From Windows Explorer you open C:\windows\system32\drivers\etc\hosts in notepad. You attempt to save the file and receive the save as dialog box. You need to ensure that you can save changes to c:\windows\system32\drivers\. What should you do?
A. Stop the windows search service.
B. Remove the inherited permissions from the file.
C. Start Windows Notepad by using elevated privileges.
D. Change the user account control (UAS) settings to Notify Me Only when programs try to make changes to my computer.
Answer: C
Explanation:
Windows 7 does not allow applications to write data to these secure locations. User Account Control (UAC)UAC is a security feature of Windows 7 that informs you when the action that you want to undertake requires an elevation of privileges. If you logged on with a user account that was a member of the local administrators group in previous versions of Microsoft Windows, such as Windows XP, you automatically had administrator- level access at all times. This, by itself, was not a problem because recommended good practice was that people logged on with accounts that were members of the local administrator group only when they needed to do something related to administration. The problem with this is that people tended to use their administrator account as their normal user account. It was convenient for them because they did not have to log off and log on again each time they wanted to do something related to systems administration. Unfortunately, this behavior presented a security problem because any program run by a user logged on with an administrative account runs with the rights and privileges of that user. UAC resolves this problem by allowing a user that is a member of the local Administrators group to run as a standard user most of the time and to briefly elevate their privileges so that they are running as administrators when they attempt to carry out specific administration-related tasks.Privilege elevationAll users of clients running Windows 7 run with the rights of a standard user. When a user attempts an act that requires administrative privileges, such as creating a new user account, her rights need to be raised from those of a standard user to those of an administrative user. This increase in rights is termed privilege elevation. UAC is a gateway to privilege elevation. It allows users who are members of the local Administrators group to access administrative rights, but ensures that the person accessing the Administrative rights is aware that they are doing so. This privilege elevation occurs only for a specific task. Another task executed at the same time that also requires privilege elevation generates its own UAC
QUESTION 39
You have a computer that runs Windows 7. The network contains a monitoring server named server1. The computer runs a monitoring service named Service1. Service1 uses Remote Procedure Calls (RPCs). You need to ensure that Service1 can receive requests from Server1. What should you do?
A. From windows Firewall with Advanced Security, create a predefined rule.
B. From windows Firewall with Advanced Security, create a custom rule.
C. From the Network and Sharing Center, modify the network location settings.
D. From the Network and Sharing Center, modify the advanced sharing settings.
Answer: B
Explanation:
Creating WFAS Rules
The process for configuring inbound rules and outbound rules is essentially the same: In the WFAS console, select the node that represents the type of rule that you want to create and then click New Rule. This opens the New Inbound (or Outbound) Rule Wizard. The first page, allows you to specify the type of rule that you are going to create. You can select between a program, port, predefined, or custom rule. The program and predefined rules are similar to what you can create using Windows Firewall. A custom rule allows you to configure a rule based on criteria not covered by any of the other options. You would create a custom rule if you wanted a rule that applied to a particular service rather than a program or port. You can also use a custom rule if you want to create a rule that involves both a specific program and a set of ports. For example, if you wanted to allow communication to a specific program on a certain port but not other ports, you would create a custom rule.
QUESTION 40
You have a customized image of Windows 7 Professional. You mount the image and modify the contents of the image. You need to restore the image to its original state. Which tool should you use?
A. Dism.exe
B. Ocsetup.exe
C. Pkgmgr.exe
D. Sysprep.exe
Answer: A
Explanation:
Dism
Deployment Image Servicing and Management (DISM) is a command-line tool used to service Windows images offline before deployment. You can use it to install, uninstall, configure, and update Windows features, packages, drivers, and international settings. Subsets of the DISM servicing commands are also available for servicing a running operating system. Windows 7 introduces the DISM command-line tool. You can use DISM to service a Windows image or to prepare a Windows PE image. DISM replaces Package Manager (Pkgmgr.exe), PEimg, and Intlcfg in Windows Vista, and includes new features to improve the experience for offline servicing. You can use DISM to perform the following actions:
* Prepare a Windows PE image.
* Enable or disable Windows features within an image.
* Upgrade a Windows image to a different edition.
* Add, remove, and enumerate packages.
* Add, remove, and enumerate drivers.
* Apply changes based on the offline servicing section of an unattended answer file.
* Configure international settings.
* Implement powerful logging features.
* Service operating systems such as Windows Vista with SP1 and Windows Server 2008.
* Service a 32-bit image from a 64-bit host and service a 64-bit image from a 32-bit host.
* Service all platforms (32-bit, 64-bit, and Itanium).
* Use existing Package Manager scripts.
DISM Command-Line Options
To service a Windows image offline, you must apply or mount it. WIM images can be mounted using the WIM commands within DISM, or applied and then recaptured using ImageX. You can also use the WIM commands to list the indexes or verify the architecture for the image you are mounting. After you update the image, you must dismount it and then either commit or discard the changes you have made.
NOT Sysprep
Sysprep is a tool designed for corporate system administrators, OEMs, and others who need to deploy the Windows XP operating system on multiple computers. After performing the initial setup steps on a single system, you can run Sysprep to prepare the sample computer for cloning. Sysprep prepares the image for capture by cleaning up various user-specific and omputerspecific settings, as well as log files. The reference installation now is complete and ready to be imaged.
http://www.passleader.com/70-680.html
QUESTION 41
You are the network administrator for a large organization that uses both Windows Server 2008 R2 and Windows 7. One of the Windows 7 machines needs to be backed up daily. You perform an image backup on the Windows 7 machine. The Windows 7 machine then gets struck by a virus and will not start up properly. What can you do to get the Windows 7 machine up and running the fastest possible way?
A. Because of the virus, the best thing is to rebuild the machine from scratch.
B. Start the computer from the Windows 7 DVD and then use the System Image Recovery tool.
C. Start the computer from the Windows 7 DVD and then use the Image Restore utility.
D. Use a Windows 7 boot disk and run the Image Restore utility.
Answer: B
Explanation:
After starting the machine with the Windows 7 DVD, you can use the System Image Recovery tool to reload the backup image that you created.
QUESTION 42
You need to back up Windows 7, but the backup must be backed up to a local disk drive. When you start the backup, you see the following screen: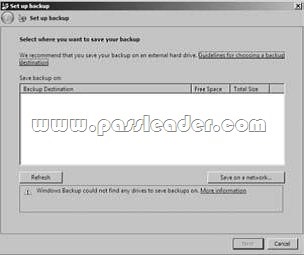
What action do you need to perform?
A. Log on as the backup administrator.
B. Log on as the system administrator.
C. Add a local hard disk to the machine by using Computer Management and then run the backup again.
D. Run the backup utility in protected mode.
Answer: C
Explanation:
When you are using the backup utility and no local disks are present, you must either configure an installed disk or physically install a hard disk before running the backup utility. You can also save your backups to a network location.
QUESTION 43
You are the system administrator for a large organization that uses Windows Server R2 and Windows 7. You have a Windows 7 machine and have enabled System Protection. You want the machine to retain only the last System Protection snapshot that was taken. What should you do?
A. Run Disk Cleanup for System Restore and then run Shadow Copies.
B. Disable Shadow Copies and run System Protection.
C. Set the Keep Only Last Shadow Copy option in System Protection.
D. Enable Shadow Copies and then set the Keep Only Last Shadow Copy option.
Answer: A
Explanation:
You have to run the Disk Cleanup utility to delete the previous versions and then run Shadow Copies in System Protection. There is no Keep Only Last Shadow Copy option.
QUESTION 44
You are the network administrator for a small company. You manage the computers for the marketing department, all of which are running the Windows 7 operating system. You are making several configuration changes to the manager’s computer to enhance performance. Before you make any changes, you want to create a restore point that can be used if any problems arise. How do you manually create a restore point?
A. By using the System Restore utility
B. By using the System Protection tab of the System Properties dialog box
C. By using the System Configuration utility
D. By using the Startup Repair tool
Answer: B
Explanation:
To manually create a restore point or to restore your computer to a previous restore point, you use the System Protection tab of the System Properties dialog box. Although System Restore uses restore points, you do not use the System Restore utility to create a restore point.
QUESTION 45
Your computer uses a SCSI adapter that supports a SCSI drive, which contains your Windows 7 system and boot partitions. After updating the SCSI driver, you restart your computer, but Windows 7 will not load. You need to get this computer up and running as quickly as possible. Which of the following repair strategies should you try first to correct your problem?
A. Restore your computer’s configuration with your last backup.
B. Boot your computer with the Last Known Good Configuration.
C. Boot your computer with the Safe Mode option.
D. Boot your computer to the Recovery Console and manually copy the old driver back to the computer.
Answer: B
Explanation:
If you need to get a stalled computer up and running as quickly as possible, you should start with the Last Known Good Confi guration option. This option is used when you have made changes’s hardware confi guration and are having problems restarting to your computer. The Last Known Good Confi guration will revert to the confi guration used the last time the computer was successfully booted. Although this option helps overcome confi guration errors, it will not help for hardware errors.
QUESTION 46
You have a computer that runs Windows 7. You view the properties of a file on the computer as show in the exhibit. (Click the Exhibit button.) You need to ensure that you can configure permissions on the file. What should you do? 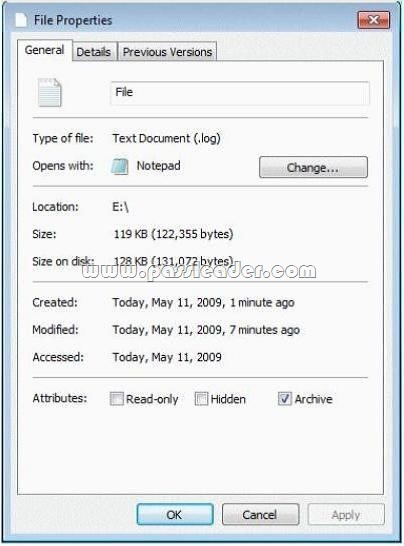
A. From Folder Options, modify the View settings.
B. Move the file to a disk that has the NTFS file system.
C. Open Windows Explorer by using elevated privileges.
D. Hold the SHIFT key, right-click the file, and click Properties.
Answer: B
Explanation:
Missing options hints not on NTFS. On NTFS volumes, you can set security permissions on files and folders. These permissions grant or deny access to the files and folders. You can view security permissions for files and folders by completing the following steps:
1. In Windows Explorer, right-click the file or folder you want to work with.
2. From the pop-up menu, select Properties, and then in the Properties dialog box click the Security tab.
3. In the Name list box, select the user, contact, computer, or group whose permissions you want to view. If the permissions are dimmed, it means the permissions are inherited from a parent object.
QUESTION 47
You attach a mobile device that runs Windows Mobile Professional 6.1 to a computer. You discover that windows is unable to install the necessary device drivers for the mobile device. You need to ensure that you can synchronize file to the mobile device. What should you do?
A. From Windows Mobility Center, click Sync settings.
B. From Sync Center, click set up new sync partnerships.
C. From Device Manager, click scan for hardware changes.
D. From Devices and Printers, right-click the device and click troubleshoot.
Answer: D
Explanation:
You cannot sync without the drivers installed. It says unable to install, assuming that it could find the device if it was able to reach attempting to install point. Therefore Troubleshoot.
QUESTION 48
You install an application named app1.exe on a computer. After the installation the computer becomes unresponsive. You restart the computer and attempt to uninstall App1.exe. The uninstallation of App1.exe fails. You need to restore the computer to its previous functional state. You must achieve the goal by using the minimum amount of administration. What should you do?
A. From Recovery, restore a system restore point.
B. From the Previous Versions tab of App1.exe, click Restore button.
C. Start the computer, press F8 and then use the Last Known Good Configuration.
D. Create a system repair disc and then start the computer from the system repair disc.
Answer: A
Explanation:
If you install an application that causes your computer to become unstable, you should first attempt to uninstall the application. If this does not solve the problem, you can restore system files and settings by performing a system restore to restore the computer to its last system restore point. A system restore returns a computer system to a selected restore point. System restores do not alter user files. Note that a system restore is not the same as a System Image restore. Windows 7 creates system restore points on a regular schedule and prior to events such as the installation of applications and drivers. A restore point contains information about registry settings and other system information. Windows 7 generates restore points automatically before implementing significant system changes. You can manually create restore points and restore a computer system to a selected restore point. If you install an application or driver that causes your computer to become unstable, you should first attempt to uninstall the application or roll back the driver. If this does not solve the problem, you can restore system files and settings by performing a system restore to restore the computer to its last system restore point. A system restore returns a computer system to a selected restore point. System restores do not alter user files. Note that a system restore is not the same as a System Image restore.
QUESTION 49
You have a portable computer named Computer1 and a desktop computer named Computer2. Both computers run Windows 7. On computer2, you create a share named Share1 by using Advanced Sharing feature. You need to ensure that when you connect to Share1 from Computer1, the files that you open are automatically cached. What should you do?
A. On Computer1, modify the Offline Files settings.
B. On Computer1, modify the User Profile settings.
C. On Computer2, modify the properties of Share1.
D. On Computer2, modify the file sharing connection settings for the HomeGroup.
Answer: C
QUESTION 50
You have a computer that runs Windows 7. The computers hard disks are configured as shown in the following table: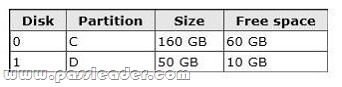
You need to ensure that you can recover the operating system and all the files on the computer if both hard disks fail. Which two actions should you perform? (Each correct answer presents a part of the solution. Choose two.)
A. Create a system image.
B. Create a system repair disc.
C. Shrink C and then create a new partition.
D. Connect an external hard disk to the computer.
Answer: AD
Explanation:
A System Image is a copy of all the files and folders on the system disk (and other specified hard disks) on a computer. You can use a System Image backup to restore the computer to exactly what its configuration was when the System Image backup was created. External hard drives can be removed and stored in a secure location.NOT System Repair Disc:A system repair disc can be used to boot your computer. It also contains Windows system recovery tools that can help you recover Windows from a serious error or restore your computer from a system image. It does not actually save the data and will only help if a system image exists elsewhere.NOT Shrink: All partitions are inaccessible is a hard disk fails.
