PassLeader’s 290q 70-687 vce dumps and pdf dumps help passing 70-687 exam! PassLeader nowadays provide the new version 70-687 exam questions with vce and pdf for free download, the latest 70-687 study guide and practice test tell you all details about exam 70-687, you can acquire the 70-687 certification easily by learning PassLeader’s 290q 70-687 premium vce file and pdf dumps. Now visit passleader.com and download free 70-687 exam dumps and you will pass 70-687 exam the other day.
keywords: 70-687 exam,290q 70-687 exam dumps,290q 70-687 exam questions,70-687 pdf dumps,70-687 vce dumps,70-687 study guide,70-687 practice test,Configuring Windows 8.1 Exam
QUESTION 211
You use a computer that has Windows 7 Professional (32-bit) installed. You need to migrate the computer to Windows 8.1 Pro (64-bit). Which installation method should you use?
A. Download and run Windows 7 Upgrade Advisor.
B. Download and run Windows 8.1 Upgrade Assistant.
C. Start Windows 8.1 custom installation from a DVD.
D. Open Windows Anytime Upgrade.
Explanation:
http://windows.microsoft.com/en-us/windows-8/upgrade-to-windows-8
Update to Windows 8.1: FAQ
Can I update from a 32-bit version of Windows to a 64-bit version of Windows 8.1?
If your PC has a 64-bit capable processor (CPU) but is currently running a 32-bit version of Windows, you can install a 64-bit version of Windows 8.1, but you’ll need to buy it as a DVD and perform a clean installation. You won’t be able to keep any files, settings, or apps when you update from a 32-bit to a 64-bit version.
QUESTION 212
A company has Windows 8.1 client computers. All user data is stored locally. Each data file has a system access control list (SACL). You need to ensure that an event is generated when a user modifies a local file. Which audit policy setting should you configure?
A. Audit process tracking
B. Audit policy change
C. Audit object access
D. Audit privilege use
Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/cc776774%28v=ws.10%29.aspx
Audit object access
This security setting determines whether to audit the event of a user accessing an object– for example, a file, folder, registry key, printer, and so forth–that has its own system access control list (SACL) specified. If you define this policy setting, you can specify whether to audit successes, audit failures, or not audit the event type at all. Success audits generate an audit entry when a user successfully accesses an object that has an appropriate SACL specified. Failure audits generate an audit entry when a user unsuccessfully attempts to access an object that has a SACL specified.
QUESTION 213
A company has Windows 8.1 client computers. A client computer named COMPUTER1 has a shared folder named Computer1 located in the user’s Downloads folder. Computer1 is shared only with employees in the Marketing department. All Marketing employees can connect to Computer1 from their client computers. A Marketing employee is unable to connect to Computer1 from a legacy device that is not compatible with the Windows 8.1 default sharing settings. The device is able to connect to resources on other client computers. You need to configure COMPUTER1 to allow the device to connect to Computer1. Which setting should you enable?
A. Turn off network discovery
B. Use 128-bit encryption to help protect file sharing connections
C. Turn on sharing so anyone with network access can read and write files in the Public folders
D. Enable file sharing for devices that use 40- or 56-bit encryption
E. Turn off password protected sharing
Answer: D
QUESTION 214
Hotspot Question
You administer Windows 8.1 Pro computers in your company network, including a computer named Client1. On Client1, you create a new folder named C:\Folder1 and configure its NTFS permissions. You need to ensure that only members of a group named Managers can access the folder content. In the Advanced Security Settings for Folder1 pane, which security setting should you configure? (To answer, select the appropriate setting in the answer area.)
Answer: 
QUESTION 215
You administer Windows 8.1 computers in your company network. Music files with the MP3 extension are opening in the Music Windows Store app. You need to ensure that MP3 files always open in the Windows Media Player desktop application. What should you do?
A. From Control Panel, open Default Programs, open Set your default programs, and then in associations for Music, clear the .mp3 selection.
B. From Windows Media Player, select Options, and then on the Player tab, select the Add local media files to library when played option.
C. Right-click an MP3 file, select Open With, choose default program, and then select Windows Media Player with the use this app for all .MP3 files option selected.
D. From Control Panel, open Default Programs, open Change AutoPlay setting, and then select the Play (Windows Media Player) setting for Music.
Answer: C
QUESTION 216
A Windows 8.1 computer hosts multiple virtual machines. The computer contains one hard drive with two partitions. You need to configure a new virtual machine to use the second physical partition of the host computer as the primary boot device. What kind of virtual hard disk should you use?
A. Pass-through
B. Fixed-size
C. Differencing
D. Dynamic
Answer: A
Explanation:
http://windowsitpro.com/virtualization/hyper-v-disk-configuration-options
Hyper-V Disk Configuration Options
VHDs: Fixed, Dynamic, Differencing
By default, new VMs are created with an attached VHD. These disks represent Microsoft’s open format for virtual disks, and they have some very useful benefits.
Another important consideration with Hyper-V disks is managing storage capacity. Hyper-V has three options for creating new VHDs: fixed size, dynamically expanding, and differencing. As you can probably guess, fixed-size VHDs provision the entire disk size as the disk is created. Dynamically expanding disks consume only as much space as is actually used by data on the disk.
Differencing VHDs let you link multiple VHDs to one another.
Pass-Through Disks
Yet another type of disk, called a pass-through disk, isn’t a VHD at all. These disks are created by attaching a disk volume to a Hyper-V host, typically through either an iSCSI or Fibre Channel connection. After the disk volume is attached to the Hyper-V host, the disk is then passed through to an awaiting VM–hence the name.
Further Information:
http://blogs.technet.com/b/askcore/archive/2008/10/24/configuring-pass-through-disks-in-hyper-v.aspx
Configuring Pass-through Disks in Hyper-V
QUESTION 217
You attach an external drive to a Windows 8.1 computer. You need to ensure that scheduled defragmentation does not run on the external drive. What should you do?
A. Disable write caching on the external drive.
B. Run the defrag command and configure the schedule settings.
C. Run the diskpart command and select the external drive.
D. Configure the Optimize Drives setting to exclude the external drive.
Answer: D
http://www.eightforums.com/tutorials/8616-optimize-drives-schedule-change-windows-8-a.html
How to Change “Optimize Drives” Schedule Settings in Windows 8 and 8.1
Optimize Drives, previously called Disk Defragmenter, helps to optimize the different types of drives that PCs use today. No matter which type of drive your PC uses, Windows automatically chooses the optimization that’s right for your drive. By default, Optimize Drives runs automatically on a weekly schedule during the time you have set for automatic maintenance. But you can also optimize drives on your PC manually.
QUESTION 218
You administer Windows RT tablets in your company network. All users in the company have Microsoft Exchange Server 2010 mailboxes and access them by using Outlook Web Access or Outlook 2010. All tablets are registered on the Microsoft Exchange server as mobile devices. A user informs you that he has lost his tablet. The user is able to connect to the company network from his home computer. You need to delete Microsoft Exchange information from the lost tablet. Which application should you use?
A. Outlook 2010
B. Outlook Web Access
C. Active Directory Users and Computers
D. Routing and Remote Access Server
Answer: B
Explanation:
http://office.microsoft.com/en-us/outlook-help/delete-all-information-from-your-lost-phone-or-tablet-HA102834573.aspx
Delete all information from your lost phone or tablet
If you use your phone or tablet to access your mailbox, your phone or tablet likely stores a lot of sensitive information, such as personal identification or confidential communications.
If you lose your phone, you should immediately remove all information from the phone.
You can do that from your mailbox by using a process called remote device wipe.
Important
You can only clear the data from a device if it was set up to use Exchange ActiveSync. If you’re not sure whether your phone was set up to use Exchange ActiveSync, you can simply try the procedure below and find out. For more information, see “What else do I need to know?” later in this topic.
Remove all data from your phone or tablet
Sign in to your account using Outlook Web App. For help signing in to your account, see Sign in to Outlook Web App.
In Outlook Web App, on the toolbar, click Settings GearIcon > Options < phone < mobile devices.
Select the phone or tablet that you want to wipe.
Click Wipe Device.
Click OK.
Click Remove Phone from List.
Further Information:
http://oxfordsbsguy.com/2014/05/19/how-to-remote-wipe-a-mobile-phone-using-outlook-web-access/
QUESTION 219
Two Windows 8.1 computers named COMPUTER1 and COMPUTER2. You connect from COMPUTER1 to COMPUTER2 by using Remote Desktop. You are unable to copy any files between COMPUTER1 and COMPUTER2 during the Remote Desktop session. You need to ensure that you can copy files between the computers during the Remote Desktop session. What should you do?
A. On COMPUTER1, open Remote Desktop Connection and configure the Local devices and resources settings.
B. On COMPUTER2, add COMPUTER1 to the trusted hosts in Windows Remote Management (WinRM).
C. On COMPUTER2, open Remote Desktop Connection and configure the Local devices and resources settings.
D. On COMPUTER1, add COMPUTER2 to the trusted hosts in Windows Remote Management (WinRM).
Answer: A
QUESTION 220
You administer Windows 8.1 Pro computers in your company network. All computers are members of an Active Directory Domain Services (AD DS) domain. A server named Server1 runs Windows Server 2012 and has an IP address of 10.10.10.20. Server1 is configured to use port 10987 for Remote Desktop connections. From your Windows 8.1 computer, you need to create a Remote Desktop connection to Server1. What should you do?
A. From the General tab of your Remote Desktop connection, enter 10.10.10.20 port: 10987.
B. Create a new Remote Desktop connection, and then set the Local Computer policy to Disable drives redirection for Remote Desktop Services.
C. From the Advanced tab of your Remote Desktop connection, configure the port of Server1 in the server authentication field.
D. Run mstsc.exe /v:10.10.10.20:10987.
Answer: D
http://www.passleader.com/70-687.html
QUESTION 221
Drag and Drop Question
A company has 100 client computers. The company plans to deploy Windows 8.1 to the client computers and utilize the following features:
– Microsoft Hyper-V 3.0
– Snap
– Secure boot
You need to establish whether the current hardware supports the features. What hardware is required to enable each of the features? (To answer, drag the appropriate hardware requirements to the correct location or locations in the answer area. Requirements may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
Answer: 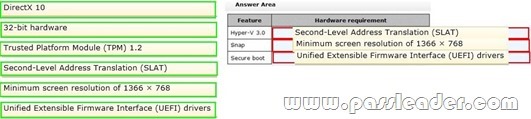
QUESTION 222
Drag and Drop Question
You administer Windows 8.1 client computers in your company network. A computer has a simple (no resiliency) storage space configured. The storage space is assigned to drive letter E. You plug an eSATA drive into the computer and extend the storage space. You need to unplug the eSATA drive without deleting existing data from the storage space. Which three actions should you perform in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)
Answer: 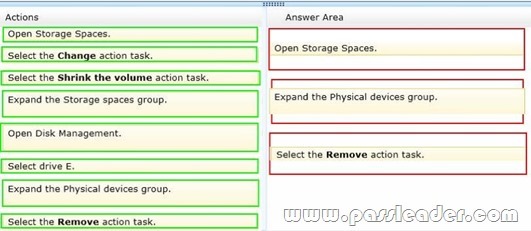
QUESTION 223
Drag and Drop Question
You manage Windows 8.1 client computers. You have the following client computer update requirements:
– Ensure that all client computers check for updates twice a day.
– Install all critical and available updates, including updates that require a restart, each day.
– Restart client computers at 11:00 P.M. if required.
– Distribute all updates from a Windows Server Update Services (WSUS) server on the local network
You need to deploy Group Policy settings to the client computers to meet the update requirements. Which Group Policy settings should you enable and configure? (To answer, drag the appropriate Group Policy settings to the correct location or locations in the answer area. Group Policy settings may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
Answer: 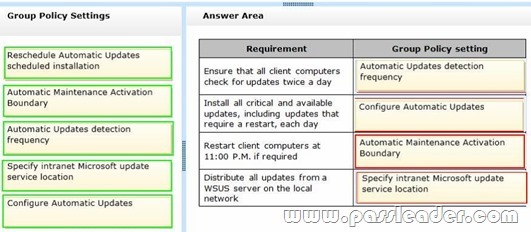
QUESTION 224
A portable computer that runs Windows 8 uses a mobile broadband connection for the corporate wireless network. The computer also has a wired corporate network connection. The computer successfully downloads Windows updates when connected to either network. You need to ensure that the computer automatically downloads updates by using Windows Update while also connected to the wireless corporate network connection. What should you do?
A. Set the corporate wireless network to metered.
B. Set the corporate wireless network to non-metered.
C. Configure the Specify intranet Microsoft update service location local Group Policy setting.
D. Configure a Windows Firewall connection security rule.
Answer: B
Explanation:
Setting a Wireless network to METERED allows only critical Windows Updates using that connection. Setting a Wireless network to NON-METERED allows all Windows Updates using that connection.
Source: http://windows.microsoft.com/en-US/windows-8/metered-internet-connections-frequently-asked-questions
QUESTION 225
A company has an Active Directory Domain Services (AD DS) domain. All client computers run Windows 8.1 and are joined to the domain. All client computers are shared. Employees can log on to any client computer by using individual accounts. The company implements a new security policy. You have the following requirements:
– Ensure that each employee can log on to all computers by using his or her account.
– Ensure that employees can reset their credentials from any client computer.
You need to choose authentication methods that meet the requirements. Which two authentication methods meet the requirements? (Each correct answer presents a complete solution. Choose two.)
A. Active Directory user account
B. Local user account
C. Microsoft account
D. Pin
E. Picture password
Answer: AC
Explanation:
http://windows.microsoft.com/en-us/windows-8/connect-microsoft-domain-account
Connect your Microsoft account to your domain account
You can connect your Microsoft account to your domain account and sync your settings and preferences between them. For example, if you use a domain account in the workplace, you can connect your Microsoft account to it and see the same desktop background, app settings, browser history and favorites, and other Microsoft account settings that you see on your home PC. You’ll also be able to use Microsoft account services from your domain PC without signing in to them individually.
QUESTION 226
A company has Windows 8.1 client computers. A user stores files in multiple locations. You need to determine which of the locations will be included in File History. Which three of the following file locations are included in File History? (Each correct answer presents part of the solution. Choose three.)
A. %appdata%
B. Public Documents and Public Pictures
C. My Documents and My Pictures
D. Contacts, Desktop, and Favorites
E. C:\Program Files
F. All user profile folders
Answer: BCD
Explanation:
http://blogs.msdn.com/b/b8/archive/2012/07/10/protecting-user-files-with-file-history.aspx
Protecting user files with File History
File History is a backup application that continuously protects your personal files stored in Libraries, Desktop, Favorites, and Contacts folders. It periodically (by default every hour) scans the file system for changes and copies changed files to another location. Every time any of your personal files has changed, its copy will be stored on a dedicated, external storage device selected by you. Over time, File History builds a complete history of changes made to any personal file.
It’s a feature introduced in Windows 8 that offers a new way to protect files for consumers.
It supersedes the existing Windows Backup and Restore features of Windows 7.
File History only saves copies of files that are in your libraries, contacts, favorites, and on your desktop. If you have folders elsewhere that you want backed up, you can add them to one of your existing libraries or create a new library.
http://www.dummies.com/how-to/content/back-up-your-computer-with-windows-8-file-history.html
Back Up Your Computer with Windows 8 File History
File History backs up everything in your libraries: Documents, Music, Pictures, and Videos, as well as the Public folders. That’s natural because that’s where you store your files.
QUESTION 227
You use a Window 8.1 tablet. The tablet receives Windows Update updates automatically from the Internet. The tablet has Wi-Fi and is connected to a 3G mobile broadband Wi-Fi hot spot. You need to minimize data usage while connected to this hot spot. What should you do?
A. Edit the Inbound Rule of Windows Firewall, and then disable Internet Control Message Protocol (ICMP) traffic.
B. Configure the broadband connection as a metered network.
C. Configure the interface metric of IP settings for Wi-Fi connection as 1.
D. Turn on Airplane Mode.
E. Disable File and Print Sharing for mobile broadband connections.
Answer: B
Explanation:
http://windows.microsoft.com/en-us/windows-8/metered-internet-connections-frequently-asked-questions
Metered Internet connections: FAQ
If you have a metered Internet connection, setting your network connection to metered in Windows can help you reduce the amount of data you send and receive.
Note: Ethernet network connections can’t be set to metered.
How does setting my network connection to metered affect my PC?
Any app that relies on an Internet connection to update or display info might be limited in the amount of data it can download or display.
You might notice these and other effects:
Windows Update will only download priority updates.
Apps downloading from the Windows Store might be paused.
Start screen tiles might stop updating.
Offline files might not sync automatically.
QUESTION 228
A company has Windows 8.1 client computers. You are designing a remote management solution. IIS is installed on some remote computers and configured to use port 80 and port 443. You have the following requirements:
– Ensure that you can perform most of the same tasks through the remote management solution that you can while working directly on the remote computer.
– Ensure that the solution can operate on port 80 and on port 443.
You need to choose the remote management tool to meet the requirements. Which remote management tool should you choose?
A. Windows Remote Shell (WinRS)
B. Remote Desktop Connection (RDC)
C. Network Shell (netsh)
D. Windows Management Instrumentation (WMI)
Answer: A
Explanation:
http://blogs.technet.com/b/jonjor/archive/2009/01/09/winrm-windows-remote-management-troubleshooting.aspx
What is WinRM?
New in Windows Vista, Windows Server 2003 R2, Windows Server 2008 (and Server 2008 Core) are WinRM & WinRS. Windows Remote Management (known as WinRM) is a handy new remote management service. WinRM is the “server” component of this remote management application and WinRS (Windows Remote Shell) is the “client” for WinRM, which runs on the remote computer attempting to remotely manage the WinRM server. However, I should note that BOTH computers must have WinRM installed and enabled on them for WinRS to work and retrieve information from the remote system.
While WinRM listens on port 80 by default, it doesn’t mean traffic is unencrypted. Traffic by default is only accepted by WinRM when it is encrypted using the Negotiate or Kerberos SSP. WinRM uses HTTP (TCP 80) or HTTPS (TCP 443). WinRM also includes helper code that lets the WinRM listener to share port 80 with IIS or any other application that may need to use that port.
What is WinRS?
Remote Shell, (WinRS) is used to execute a program on a remote host.
QUESTION 229
You add three hard drives to a Windows 8.1 computer. The computer has a RAID controller. You plan to store data only on the three new hard drives. You need to ensure that data loss will not occur if only one hard drive fails. What should you do?
A. Create a storage pool that contains all drives and set the resiliency type to Parity.
B. Create a storage pool that contains one drive, and then add the other two drives drive to the pool.
C. Create a spanned volume.
D. Create a storage pool that contains all drives and set the resiliency type to Two-way mirror.
Answer: A
QUESTION 230
You administer a Windows 8.1 computer that runs Hyper-V. The computer hosts a virtual machine with multiple snapshots. The virtual machine uses one virtual CPU and 512 MB of RAM. You discover that the virtual machine pauses automatically and displays the state as paused-critical. You need to identify the component that is causing the error. Which component should you identify?
A. Insufficient hard disk space
B. Insufficient number of virtual processors
C. No virtual switch defined
D. Insufficient memory
Answer: A
Explanation:
http://blogs.msdn.com/b/virtual_pc_guy/archive/2009/04/22/why-is-my-virtual-machine-paused-critical-hyper-v.aspx
Why is my virtual machine “Paused-Critical”? [Hyper-V]
Virtual machines will go into the “Paused-Critical” state under Hyper-V if we detect that we are going to run out of space for the virtual hard disks. If we were to run out of space for expanding a dynamic or differencing virtual hard disk -we would start failing disk write operations inside the virtual machine. The result would most likely be that the guest operating system would crash.
To avoid this problem we periodically poll the storage that is being used for the virtual hard disks. If the free space falls under 2 gigabyte we will start to log warning messages in the event log. If the free space falls under 200 megabyte we will pause the virtual machine and mark it as “Paused-Critical”.
